 Apple’s next-gen Siri isn’t arriving at WWDC 2025—and likely won’t be ready for quite a while. Despite splashy ads last year teasing a major AI overhaul, the promised upgrade remains stuck in development.
Apple’s next-gen Siri isn’t arriving at WWDC 2025—and likely won’t be ready for quite a while. Despite splashy ads last year teasing a major AI overhaul, the promised upgrade remains stuck in development.
Internally, Apple’s AI efforts have been chaotic. Senior leadership, including Software Engineering head Craig Federighi, initially saw little value in chasing generative AI. That changed only after ChatGPT’s release in late 2022. Executives quickly shifted gears, hoping to pack iOS 18 with AI-driven tools. [Read more…]
 Microsoft will continue rolling out security updates for Microsoft 365 apps on Windows 10 until October 2028, extending support three years past the operating system’s planned end-of-life.
Microsoft will continue rolling out security updates for Microsoft 365 apps on Windows 10 until October 2028, extending support three years past the operating system’s planned end-of-life.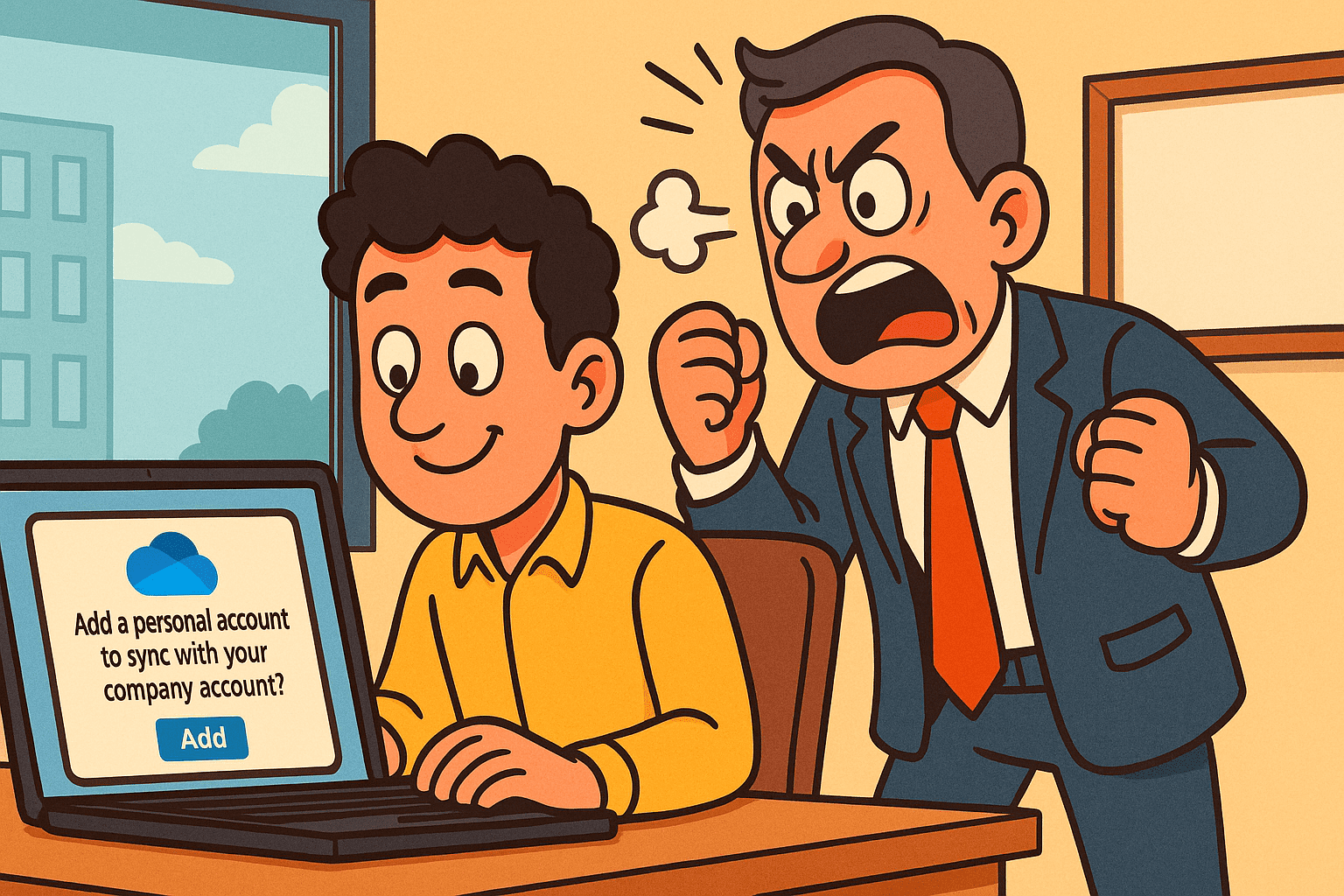 Microsoft is quietly pushing out a OneDrive update that’s catching IT departments off guard. A new feature prompts users—by default—to connect their personal OneDrive accounts to corporate machines. No setup needed. The feature just appears and offers a quick, seamless sync between personal and business storage.
Microsoft is quietly pushing out a OneDrive update that’s catching IT departments off guard. A new feature prompts users—by default—to connect their personal OneDrive accounts to corporate machines. No setup needed. The feature just appears and offers a quick, seamless sync between personal and business storage.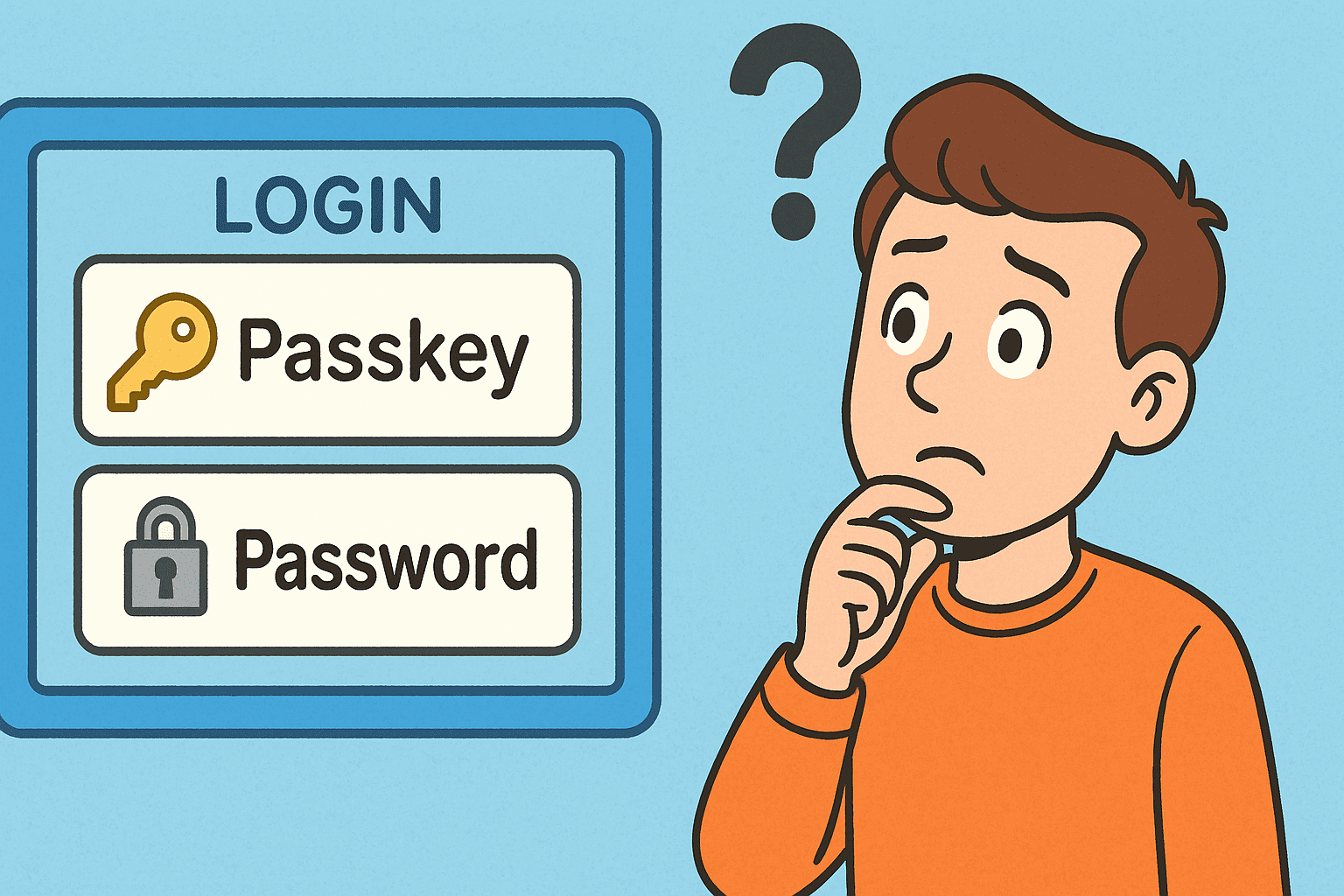 Microsoft is shifting new account signups away from passwords and toward passkeys. It’s part of a broader industry effort, with companies like Google and Apple also pushing for a future where stolen credentials are no longer a threat. This move sounds like progress, but there’s more going on beneath the surface.
Microsoft is shifting new account signups away from passwords and toward passkeys. It’s part of a broader industry effort, with companies like Google and Apple also pushing for a future where stolen credentials are no longer a threat. This move sounds like progress, but there’s more going on beneath the surface. A bill designed to curb the spread of non-consensual intimate imagery (NCII), whether real or AI-generated, is on the brink of becoming law. Known as the Take It Down Act, the legislation commands online platforms to delete such material within 48 hours of being notified by victims. It’s expected to clear the House of Representatives and head swiftly to the White House, where President Donald Trump has pledged to sign it into law, aligning with First Lady Melania Trump’s strong support.
A bill designed to curb the spread of non-consensual intimate imagery (NCII), whether real or AI-generated, is on the brink of becoming law. Known as the Take It Down Act, the legislation commands online platforms to delete such material within 48 hours of being notified by victims. It’s expected to clear the House of Representatives and head swiftly to the White House, where President Donald Trump has pledged to sign it into law, aligning with First Lady Melania Trump’s strong support.